Three years after the discovery of the OpenSSL vulnerability, CIPHRON and mediaTest digital investigate how often "Heartbleed" (CVE-2014-0160) occurs today and analyze a large amount of data. The result shows that Heartbleed is by no means history.
Heartbleed was a serious mistake in the source code of the cryptography library OpenSSL that put services which use SSL/TLS to encrypt and authenticate traffic in networks under a high risk.
The vulnerability was a huge exciter as it allows to read out the memory of affected systems remotely via networks - even from the internet if the vulnerable service is accessible through it.In the worst-case an attacker could read login credentials of users or the private keys of TLS-certificates.The OpenBSD-developers decided afterwards to create a new fork called LibreSSL to clean out features from OpenSSL which are never or rarely used.
We from CIPHRON and our friends from mediaTest digital were now interested in the investigation if both of our customer bases are still exposed to a risk through this weakness and which mobile applications were still vulnerable today, three years after Heartbleed.After all, such a vulnerable app could lead to a massive lack of confidentiality or integrity of the data of our clients and other users.
To learn about this we accessed the database of mediaTest digital. In the database one could find the URLs and IPs of more than 60,000 Android- and iOS-App-Tests which count to the most used among smartphone users and to which the app can connect to if it is executed. These addresses belong, e.g., to trackers which collect data from users and backends which are essential for the operation of the applications.
We were only interested in services which use TLS for encryption and authentication at all.
Thus, we decided to investigate only services which serve HTTPS on port 443. This constraint is not really one as, from our experience, most applications use this port to connect to servers if TLS is used.
To prevent duplicates we resolved all URLs via DNS and removed double entries from the resulted IPs. This led to 74,978 single servers.
The research showed that 96 servers which serve HTTPS are still vulnerable to Heartbleed. Therefore 0.13% of the investigated services have not been patched since emerge of the weakness.
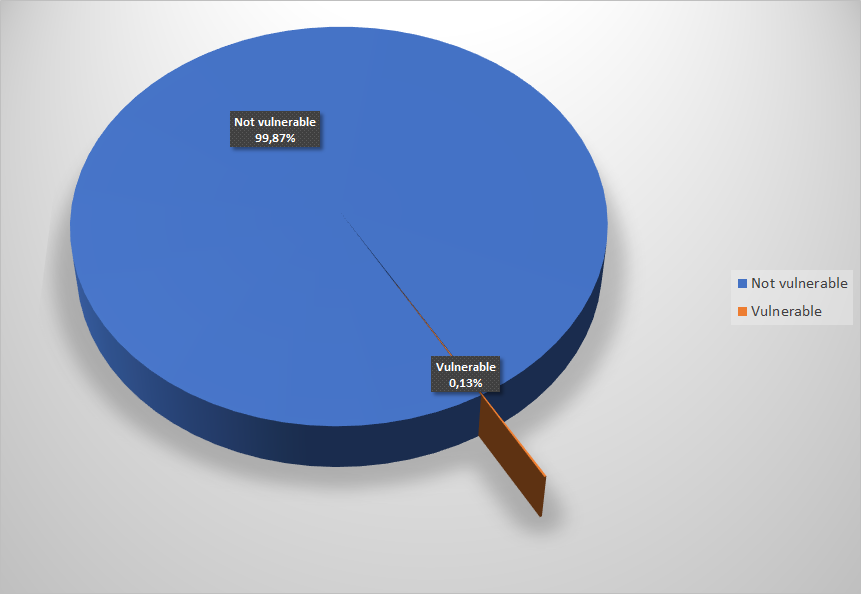
Vulnerable vs. not-vulnerable systems
For this manageable number of addresses we could do a detailed investigation what is behind them. According to the GeoIP database the biggest amout of the examined servers are stationed in the far east. 34 servers alone (35.4%) originate from China. One could find app vendors and developers among these but chinese tracking services, too.
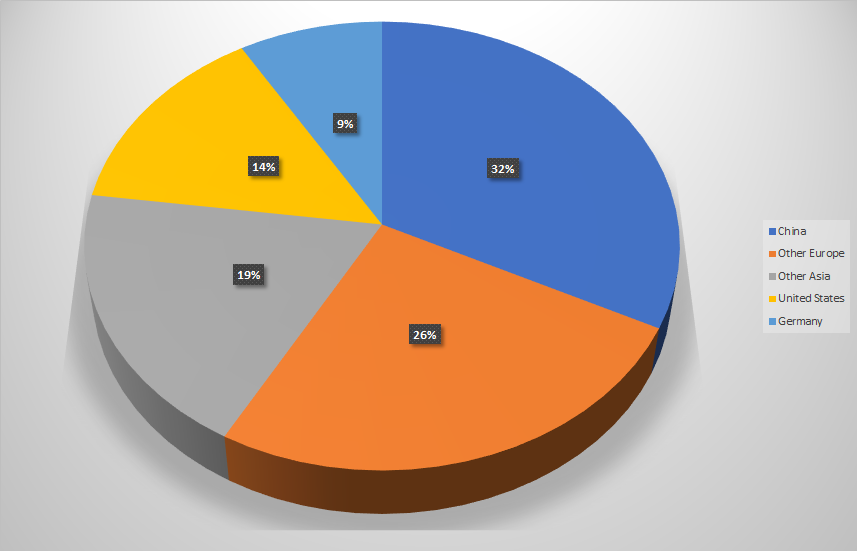
Distribution of vulnerable systems over regions
But we could identify vulnerable services which belong to anglophone and germanophone applications, too. One could find not only a german fitness app among these but also one which processes medical data. Of course we informed all identified server and app providers about our research to eradicate the last leftovers, but only few of them responded until the date of this publication.
In the end one could say that smartphone users at least do not have to worry about the Heartbleed-vulnerability anymore. Especially through the migration of most vendors and providers to content delivery networks like Cloudflare, which are zealous and transparent about the security of their clients in general, most apps are not affected by Heartbleed from the internet-facing perspective anymore.
By the way: We did a similar investigation on the current vulnerability in SMB which was called DOUBLEPULSAR.
DOUBLEPULSAR is a NSA backdoor which exploits a vulnerability in Samba and was leaked by the Shadow Brokers in the latest NSA leak. To implement the backdoor, the ETERNAL BLUE vulnerability (MS17-010) is used which was used in the recent WannaCry ransonware outbreak.
We identified exaclty one server which responded to the backdoor, i.e the server was infected with high probability. The vendor did not respond to our hint but the app which belongs to the affected server was not updated during the last five years.
Hence, we concluded that the the vendor does not actively support the application anymore resp. shifted his business activity.
If you have questions about this or other topics around application and IT security, do not hesitate to contact us:
Karsten König (kk@ciphron.de, Ciphron), among other things:
- Penetration tests
- Code reviews
- Individual research
Wulf Bolte (bolte@appvisory.com, mediaTest digital), among other things:
- App-security audits
- Automatic App white- und blacklisting incl. MDM integration
-
-
CIWATCH
IT-Monitoring
Das umfassendste KnowHow zur Überwachung Ihrer IT-Services
Mehr erfahren
-
-
CIDESK
OTOBO
Geschäftsprozesse und Kommunikation perfekt managen
Mehr erfahren
-
-
CISQUAD
Wir machen sauber
Cyber-Angriffe abwehren und
Sicherheit wieder herstellen
Mehr erfahren
-
-
CICHECK
Wir hacken Sie!
Stellen Sie Ihre Sicherheit
auf die Probe
Mehr erfahren



